In the ever-evolving landscape of cybersecurity, organizations must protect their corporate assets from both internal and external threats. Traditional network security features guarded network perimeters, which may be difficult to access from outside the network. However, they implicitly trust everyone within the network, which creates internal threats.
Enter the Zero Trust Network Architecture (ZTNA), a revolutionary approach that challenges traditional perimeter-based security models. In this blog, we will explore the concept of Zero Trust Architecture and how it helps organizations build resilient networks that withstand sophisticated cyber threats.
What is Zero Trust Network Access (ZTNA)?
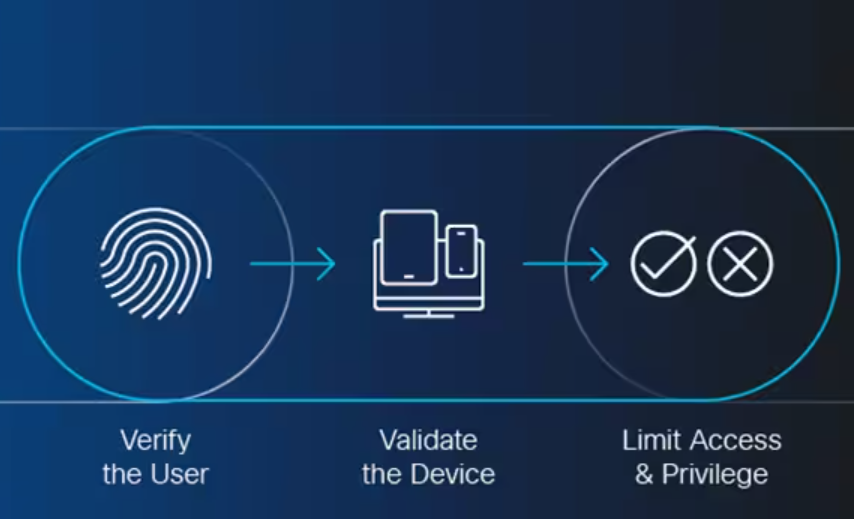
It is an IT security solution that establishes a stringent authentication process to grant access to applications, data, and services following identity and context policies. ZTNA eliminates implicit trust from the network and considers everyone accessing your critical assets as suspicious until they successfully get through the security system.
This integrated security model follows multifactor authentication, role-based access control, and identity-based user verification and device validation. With the increasing hybrid work environment, such types of granular access control help fix the gaps arising from a scattered business model.
How Does a Zero Trust Architecture Work?
Now that we have walked through the ZTNA definition and its importance for an organization and its resources let’s discuss its process in detail. Although the specific tools required to implement ZTNA may differ, these capabilities are at the core of this advanced access control strategy.
- Creating an inventory of resources that needs to be protected, classifying them on the basis of business purpose and sensitivity, and building a baseline of normal behavior.
- Managing authorization and authentication, creating resource identities, authorizing resources on the basis of device configuration, and software and hardware health checks.
- Identifying abnormalities in network usage and access in contrast to normal behavior. It also includes continuous verification of the health of resources on the network.
- Handling threat containment and implementing mitigation if a security event is spotted. For instance, separating a malicious segment from a network.
- Effectively isolating sensitive resources and restricting access to authorized entities based on specific purposes. Applying granular policies and role-based access control to protect highly sensitive information.
ZTNA Use Cases For Businesses
Vulnerabilities arise when unauthorized access is granted to users. In contrast, ZTNA grants secure access to applications, services, and networks from anywhere by checking the legitimacy of users. Here are the two core use cases of ZTNA for organizations:
Authentication and Access
The primary use case of ZTNA is to provide secure network access to end users. It works by providing granular access to workers based on their role or position in a company. By eliminating the concept of implicit trust, Zero Trust architecture fortifies the network against external and internal threats. It reduces the attack surface and minimizes the impact of potential breaches.
Besides, ZTNA offers device-specific access control measures to keep compromised devices away from your network. It leverages various technologies, such as software-defined perimeters and micro-segmentation, to create isolated and encrypted connections, ensuring that data remains protected throughout the network.
Holistic control and visibility
Once legitimate users get through the set authentication process and network infrastructure, there is still a risk of internal threats. Malicious users may use your network resources for nefarious purposes.
Though ZTNA offers continual monitoring of user and device behavior, incorporating a secure access service edge (SASE) solution in this framework will deter more internal threats. This approach enables businesses to benefit from the security and network capabilities required to secure remote access. This post-connection monitoring reduces the chances of data loss or compromised user credentials.
How To Implement A Zero Trust Network Strategy
Some of the best ways to implement ZTNA in your organization for greater network security include:
Assess Current Security Infrastructure
Start by evaluating your organization’s existing security infrastructure, including network architecture, access controls, and policies. Identify any vulnerabilities or areas that need improvement.
Define Trust Zones and Data Classification
Categorize your network and data into trust zones based on their sensitivity. This step helps determine the level of access controls and security measures needed for each zone.
Establish Strong Identity Verification
Implement robust authentication methods such as multi-factor authentication and strong passwords. Ensure that all users and devices are properly verified before granting access to resources.
Embrace the Least Privilege Principle
Apply the principle of least privilege, granting users and devices only the necessary access permissions required to perform their specific tasks. Limiting privileges can reduce the attack surface and minimizes data breach incidents.
Implement Network Segmentation
Divide your network into segments or micro-segments to create isolated environments. This enables you to control and monitor traffic between segments more effectively, further reducing the attack surface.
Implement Strong Access Controls
Deploy granular access controls, such as role-based access control, to enforce strict authorization policies. This ensures that users can only access the resources they need to complete their work.
Implement Continuous Monitoring and Threat Detection
Employ advanced monitoring tools to continuously monitor network traffic, user behavior, and device health. Detect and respond to any anomalies promptly to prevent potential security incidents.
Adopt ZTNA Solutions
Now consider implementing Zero Trust solutions to provide secure remote access to resources. ZTNA employs technologies like software-defined perimeters (SDPs) and virtual private networks (VPNs) to establish secure connections.
Educate and Train Employees
Conduct comprehensive training programs to educate employees about Zero Trust principles, the importance of secure practices, and how to recognize and report potential security threats.
Regularly Update and Test Security Measures
Keep your security measures up to date by patching vulnerabilities and regularly testing your network’s resilience through penetration testing and security assessments.
Monitor and Maintain
Continuously monitor the effectiveness of your Zero Trust strategy and make necessary refinements as new threats and technologies emerge. Zero Trust strategy formulation is an ongoing process, so you need to stay ahead of the latest trends in the security realm.
Final Words
As cyber threats continue to evolve in sophistication, adopting a Zero Trust architecture becomes imperative for organizations seeking to build resilient networks. Not only does it protect your critical resources by establishing stringent policies, but it also enables continuous monitoring of your applications and devices.
By implementing strict identity verification, granular access controls, and continuous monitoring, organizations can enhance their security posture and effectively protect their critical assets. Zero Trust network strategy plays a vital role in providing secure access to resources while mitigating risks. Embracing the Zero Trust mindset empowers you to navigate the complex cybersecurity landscape with confidence, safeguarding your data and maintaining business continuity.