In computer networks, the Domain Name System, or DNS, converts domain names into IP addresses that computers use to interact with one another. Nearly every computer network has DNS; it connects to other networks and is exceedingly challenging to secure because it was intended to be an open protocol. Doing harmful tasks like network reconnaissance, malware downloads, connection with command and control servers, or data transfers outside of a network may appeal to an adversary. As a result, it is essential to monitor DNS traffic in order to protect against threats.
In this article we will provide you the list of cyber attack types on DNS, so continue reading this article.
1. Domain hijacking
This kind of assault may entail alterations to your DNS servers and domain registrar, which could send your traffic to alternative locations instead of the original servers.
But, domain hijacking can also occur at the DNS level when attackers seize control of your DNS records. Domain hijacking is frequently triggered by a variety of circumstances connected to exploiting a weakness in the domain name registrar’s system.
Once the bad guys have taken control of your domain name, they’ll likely utilise it to carry out harmful deeds like creating a phoney page for payment systems like PayPal, Visa, or financial institutions. The real website that stores vital personal data like email addresses, usernames, and passwords will be copied exactly by attackers.
2. DNS flood attack
One of the most fundamental kinds of DNS attacks is this one. Your DNS servers will be targeted by the attacker in this distributed denial of service (DDoS) assault.
Because the resolution of resource records is impacted by all the hosted DNS zones, the main objective of this type of DNS flood is to simply overload your server so it can no longer handle DNS requests.
As the source is frequently a single IP address, this type of attack is easily neutralised. Yet when hundreds or thousands of servers are involved in a DDoS (Distributed Denial of Service), things can get challenging.
Many requests will be sent legally in an effort to trick defence measures, even though many of them will be immediately identified as malicious. This occasionally makes it tougher for the mitigation mechanism to do its work.
3. DNS Tunneling
Encoding data from other applications or protocols within DNS requests and responses is known as DNS tunnelling. Typically, it contains payloads of data that can commandeer a DNS server and give attackers control over the remote server and its applications.
DNS tunnelling frequently relies on a hacked system’s external network connectivity as a backdoor into an internal DNS server with network access. Controlling a server and a domain, which serves as an authoritative server and performs server-side tunnelling and data payload executable programmes, is also necessary.
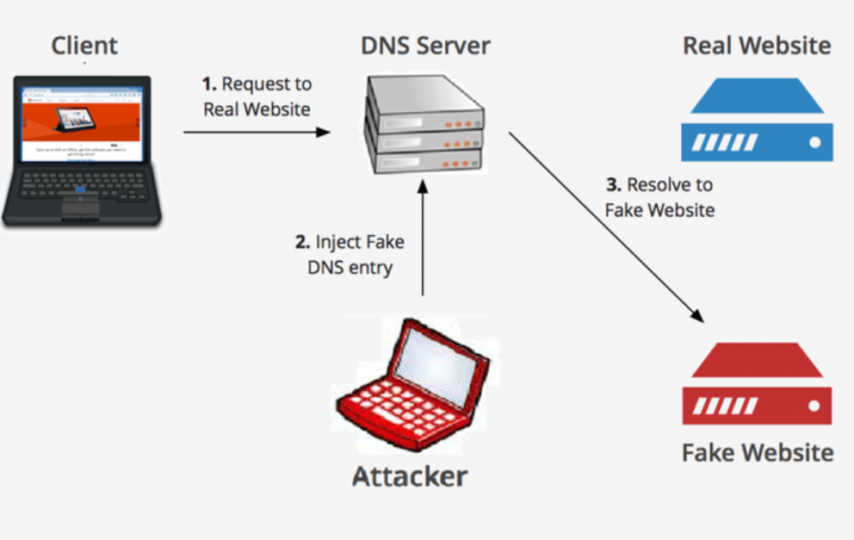
4. DNS Spoofing
DNS spoofing, also known as DNS cache poisoning, is the practise of utilising updated DNS records to reroute online traffic to a malicious website that seems to be the desired location. Users are prompted to enter into their accounts once they arrive at the phoney location.
They essentially give the threat actor the chance to steal access credentials as well as any sensitive information entered into the bogus login form after they enter the information. Furthermore, these malicious websites are frequently used to download viruses or worms onto end users’ computers, giving the threat actor ongoing access to the device and any data it holds.